Module 3. Exploring Threat Actor Types and Attributes
Types of Actors#
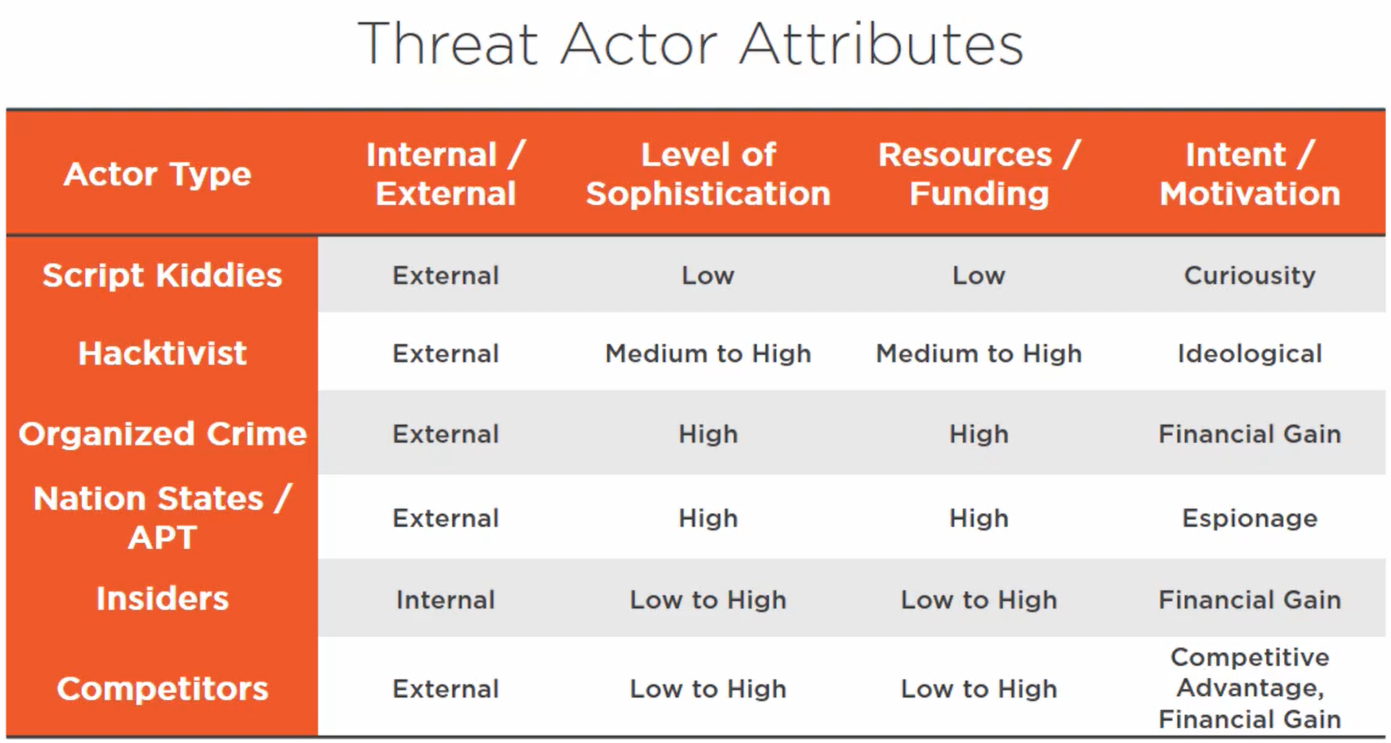
Threat actors can range from beginners probing around to highly organised nation states
Script Kiddies#
hackers are relatively new or unskilled.
- typically looking to see what they can get into
- the challenge is the attraction
- not typically associated with any groups
- Usually not well funded
Hacktivists#
hackers are motivated by ideology or some social or political cause
- can be well funded and skilled
- usually deface websites
- Steal information
- Not particularly patient or stealth
Organised Crime#
Hackers are motivated by financial gain
- Deliberate with high technical capability
- Well funded
- patient and persistent
- POS terminals, ATM machines, credit card numbers
- Steal personal information for sale on the dark web
Nation State/ Advanced Persistent Threats (APT)#
Highly skilled hackers whose main goal is to penetrate government or commercial systems. Very stealthy and persistent and well funded
- Cyber espionage
- Data/IP theft
- Sabotage
- Cyber warfare
Insiders#
Often motivated by financial gain
- CERT advises that over 70% of IP theft cases involve insiders
- Accidental exposure can occur from misuse or misconfigured systems
- Data theft includes IP and company secrets
Competitors#
Motivated by financial gain. Can be very well funded and range from low to high skill
- Competitive advantage
- Theft of IP or company secrets
- Sabotage
Threat Actor Attributes#
Use of Open Source Intelligence#
There are numerous tools and websites available for intelligence gathering and reconnaissance. Open Source Intelligence Tools (OSINT) exist as stand-alone applications, browser plugins and websites and can be passive or active in nature.
- Maltego. graphical link analysis tool for gathering and connecting information for investigative tasks.
- Metagoofil. Metagoofil is an information gathering tool designed for extracting metadata of public documents (pdf,doc,xls,ppt,docx,pptx,xlsx) belonging to a target company.
- Shodan Shodan is a search engine that lets the user find specific types of computers connected to the internet using a variety of filters.
- Google Hacking Database (GHDB). An index of search queries used to find publicly available information
- FOCA. A tool to find metadata and hidden information in the documents it scans
- EXIF Data Viewer. Extracts meta data from images mainly about the images but some images may contain GPS location image of where the photo was taken
- Kali Linux. Formally backtrack linux, is an open source linux distro geared towards security tasks such as pen tests, security research, computer forensics and reverse engineering
- Bsucador Linux. A linux distro used for online investigations. No longer updated and maintained
- The Social Engineer Toolkit. A tool designed for penetration testing around social engineering.
- PeekYou. PeekYou is a people search engine that indexes people and their links on the web, predominantly in the USA and Canada
- Wayback Machine An archive of web pages over time.
- YouGetSignal. Network tools
- Metasploit. A computer security project that provides information about security vulnerabilities